
Penetration test:
Bechtle security experts to the rescue.
When was the last time your IT security was put through its paces? Our experts are here to scrutinise your solutions. A penetration test (pen test) is an excellent and affordable method to check your IT solutions current security level. You’ll also receive a pen test breakdown of the existing weaknesses in your systems.
Why pen tests increase your company’s security level.
New security vulnerabilities in protocols and applications are constantly being reported. These are often not known at the time of implementation or new attack methods have since been developed to leverage vulnerabilities. IT systems and applications are not just our constant companions in either our private or professional environments, but merge with one another. Constant availability and the option to access company data from anywhere in the world—together with use of new technologies such as the cloud—pose new, complex challenges for IT departments.
Your benefits with Bechtle pen tests.

Protect business-critical processes.

Minimise downtime and the costs it causes.

Boost customer and partner confidence.

Security through regular checks.

Detect and successfully manage risks.

Plan of measures with security experts.

Regular pen tests lessen the attack potential for cyber threats and are an important component of any cyber defence strategy.
Patrick Pötz, Security Consultant
To keep your security level at pace with the constant change and ever more demanding requirements, pen tests are a preventative means that highlight dangers and risks and therefore an important component of every IT security strategy. Because only when you know your security vulnerabilities can you resolve them or actively protect your systems through targeted use of suitable IT security solutions.
The flexible planning of pen tests lets you get an independent and management-ready, third-party report on your company’s current security level in a relatively short time.
The Bechtle Penetration Test—as a crucial component of Bechtle’s 360 degree security solution—protects your company and toughens it against the challenges of tomorrow.
Our portfolio.
External pen test.
- Simulated attack of internet origin
- Identification of available services
- Exposing vulnerabilities, design and configuration errors
Internal pen test.
- Simulated attack of internal network origin
- Identification of available services
- Exposing vulnerabilities, design and configuration errors
Web application pen test.
- Attack on your externally or internally hosted web applications
- Identification of available services
- Exposing vulnerabilities, design and configuration errors
- Simulated attack of internet origin
- Identification of available services
- Exposing vulnerabilities, design and configuration errors
- Simulated attack of internal network origin
- Identification of available services
- Exposing vulnerabilities, design and configuration errors
- Attack on your externally or internally hosted web applications
- Identification of available services
- Exposing vulnerabilities, design and configuration errors
Wi-Fi Pen Test.
- Attacks on your Wi-Fi infrastructure
- Exposing vulnerabilities, design and configuration errors
Custom pen test.
- Attacks on your W-iFi infrastructure
- Exposing vulnerabilities, design and configuration errors
- Trainee scenario – Attacks on your clients
- Cleaning staff scenario – Attacks on your network infrastructure (LAN/WLAN)
- Tailored customer requirements
How exactly does a pen test work?
A pen test is a targeted, controlled, and planned attack on your systems. Penetration testers, also known as ethical hackers, use similar tools and attack methods to criminal attackers to identify vulnerabilities in your IT solutions. These methods and another perspective allow security vulnerabilities you and your IT team didn’t know about to be discovered. Moreover, pen tests also allow you to check how your own internal security mechanisms and IT department react to attacks.

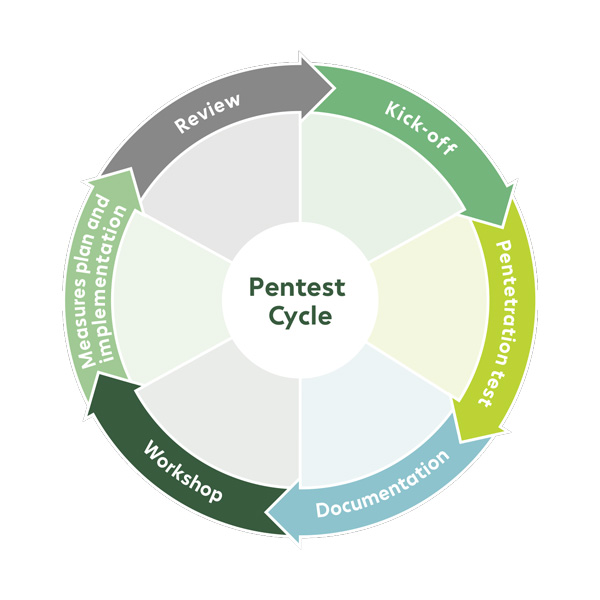
Steps of a Bechtle penetration test.
1. Kick-off
- Coordination of individual services
- Explanation of method
- Definition of test time period
2. Penetration test
- Pen test conducted according to ordered services
- Method and time period according to kick-off meeting
3. Documentation
- Documentation of vulnerabilities identified
- Risk assessment by Bechtle pen testers
- Preparation for management and technical departments
- Product-neutral recommendations and resolution of identified weaknesses
4. Workshop
- Explanation of vulnerabilities identified by the Bechtle pen testers
- Answering of open questions
- On-site or online meetings available
5. Measures plan and implementation
(internally or by Bechtle security experts)
- Creation of plan of measures
- Implementation of measures
6. Review
- Check whether vulnerabilities have been sufficiently solved
As a pen test is only a brief snapshot of the current level of security and new weaknesses or attack entry points are always becoming known, pen tests need to be carried out regularly. It is especially recommended to integrate pen tests into the development phase of new products and after changes to the infrastructure, for example.
What does a pen test cost?
As every penetration test is tailored to the customer, it’s very difficult to name a generic price.
A penetration test depends on many variables including such questions as:
- What external systems are to be checked (external, internal, web applications)?
- How many IT systems and/or web applications are to be checked?
- Selected version?
- Custom checks?
We’ll be happy to tell you more about our pen tests via an online meeting or an appointment at your site. Book a meeting today with one of our pen testers.
Want to know more about pen tests or need advice?
Get in touch with us now.
*Mandatory field.
Please read our Privacy Policy for information on how we process your data and protect your rights as a data subject.