Not all data is equal – Why classification is the key to sovereignty.
by Tim ter Haar
Written by
Digital sovereignty is more relevant than ever. Geopolitical tensions are rising, and legislation such as the US CLOUD Act is prompting European organisations to ask important questions: Is your data truly secure? Who has access to it? And how does a shifting geopolitical landscape affect your cloud strategy?
In recent years, Microsoft has taken meaningful steps to address these concerns—introducing Sovereign Cloud and making additional commitments within Europe. In this blog, we outline the key considerations and offer guidance to help your organisation make informed, strategic decisions.

Digital sovereignty isn’t a straightforward issue. While organisations increasingly seek greater control and transparency, the reality is far more nuanced. Sovereign Cloud is designed to provide a clear, practical response to these concerns—particularly within the European context.
Tim ter Haar, Alliance Manager Microsoft
The CLOUD Act – US legislation, European concerns.
The CLOUD Act allows US authorities to request access to data held by companies under US jurisdiction—even if that data is physically stored in Europe. Understandably, this raises concerns for many organisations.
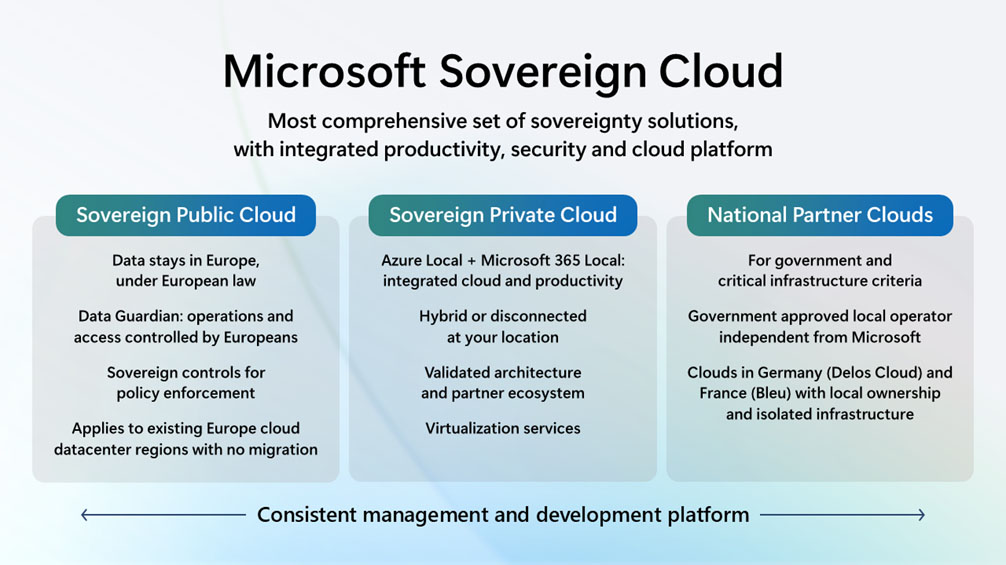
Through its Sovereign Cloud initiative, Microsoft offers several safeguards to address these issues, including:
- Data access restricted to European personnel
- Full control over encryption keys
- Entirely local management via Azure Local and Microsoft 365 Local
These measures provide greater control over your data. However, it’s important to recognise that no US-based provider can offer complete legal immunity from the CLOUD Act.
Not all data requires the same level of protection.
Digital sovereignty is about making informed choices. A common mistake is to treat all data the same and apply maximum security across the board. While this may sound safe, it often leads to unnecessary complexity, higher costs, and delays in day-to-day operations.
In reality, data varies in sensitivity, impact, and relevance. By using a data classification model, you gain clarity into which information is critical, which is confidential, and which is relatively harmless. This allows you to target your security investments effectively—without compromising productivity.
A possible classification model:
General business information.
Reports, marketing materials, or standard customer communications. For this category, storage and processing within the European Data Boundary of a public cloud is typically sufficient. The risk of unauthorised access or data loss is limited, making heavier security measures often unnecessary.
Confidential information.
HR files, financial forecasts, or customer contracts. This type of data can directly affect your organisation’s continuity and reputation. Appropriate technical measures include encryption with customer-managed keys, Customer Lockbox, and detailed logging—ensuring control remains in your hands.
Critical information.
Data related to national security, defence projects, medical records, or strategically important intellectual property. Standard cloud solutions are often not suitable for this category. In such cases, it’s worth considering on-premises environments or European cloud alternatives that fall outside US jurisdiction.

Technology is only part of the story. It starts with a clear data classification model—one that helps organisations identify which data is critical and which is less sensitive.
Tim ter Haar, Alliance Manager Microsoft
The goal of this layered approach is clear: protect what’s truly sensitive with the highest level of security, while keeping everything else agile and cost-effective. Not all data needs to sit in a tightly controlled environment—and it’s precisely this distinction that paves the way for a practical, future-proof strategy.
The ‘red button’ scenario – Myth or reality?
A commonly cited concern is that the US could shut down European cloud services at the push of a button. It sounds alarming—but the reality is far more nuanced.
Legally, Microsoft is obliged to safeguard European cloud operations.
Operationally, data centres fall under local EU jurisdiction. Economically, a sudden shutdown would be disastrous for US tech companies and their geopolitical standing.
In short, the red-button scenario is a powerful image—but not a realistic risk.
Conclusion – Bolster control, manage risk.
Digital sovereignty is no longer a theoretical debate—it’s a strategic and compliance-critical issue. Microsoft Sovereign Cloud provides a solid foundation for European organisations, with measures that reduce risk and enhance control.
That said, complete exclusion from the CLOUD Act isn’t possible as long as Microsoft remains a US-based company. The key lies in a thoughtful approach: classifying data appropriately, making informed technology choices, and implementing additional legal and organisational safeguards.
Interested in exploring what this means for your organisation? We’re here to help you gain clarity on your data landscape and identify the right measures to support it.