
HP Wolf Security.
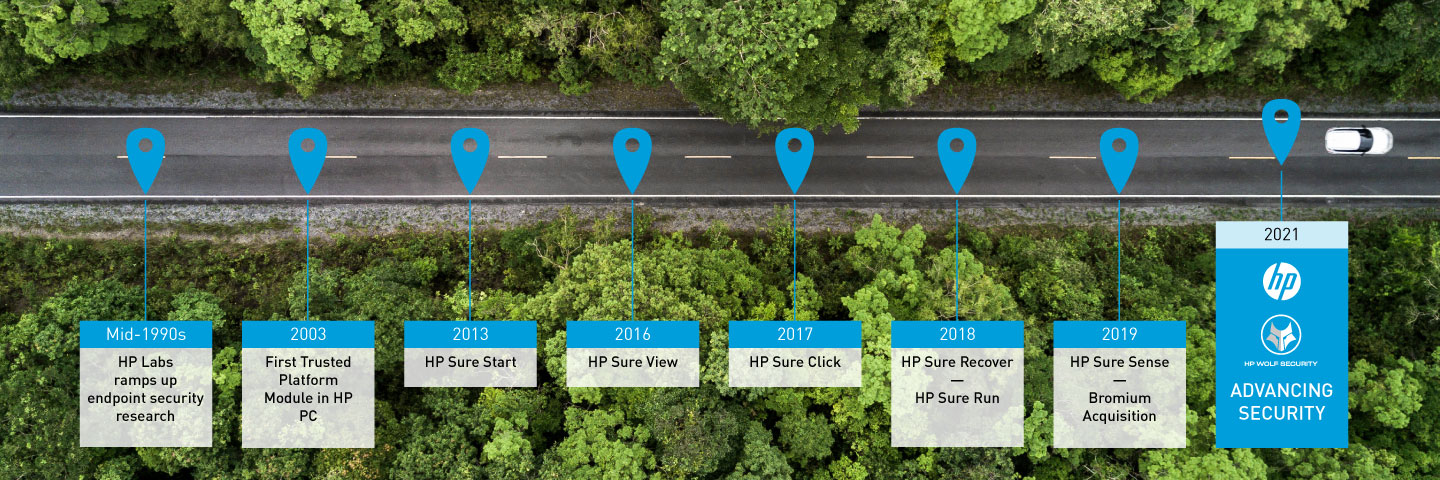
Since the 1990s, HP has not only focused on backing up hardware, but also application security. For many years, HP has been introducing consistently innovative security solutions with a focus on customer-oriented solutions that go far beyond existing PC security solutions.
The HP Wolf Pro Security Edition comes with a full next-gen antivirus system that combines AI-based technologies such as deep learning and behaviour analysis to offer advanced malware protection through predictive detection to protect against attacks.
This protection takes endpoint security to a whole new level by providing defence that is based on detection, but also isolates threats without the user noticing a thing.
The following features come with each Pro/Elite (Book and Desk) and Z-series products (mobile workstations ZBook and desktop workstations).
- Protects above, below and within the OS
- Sure Sense protects your system in real-time against unknown attacks.
- Sure Click offers reliable defence against malicious malware from the net
- Sure Start detects BIOS manipulations and recovers using backup versions
- Sure Recover can restore an image at any time.
The challenges faced by businesses have changed considerably over the last two years. Employees want more freedom to choose where they work from and often use a variety of devices to get the job done which makes it difficult to provide end users with consistent, cross-platform protection.
the target of end device attacks
over the past two years.
On your behalf, our security experts implement and manage security policies, including threat quarantine management. In this way, HP Wolf Pro Security can easily manage your endpoint security.
Once the end devices have been onboarded, we monitor their status and offer daily and weekly analyses of security incidents and attempted attacks. To ensure you are better protected against future attacks, we also carry out forensic and kill-chain analyses of previously unknown zero-day threats to determine their source.
HP Wolf Pro Security.
With HP Wolf Security, you can protect your business on multiple endpoint security layers. User can work securely from wherever they like without productivity being impacted or your IT department’s workload increasing.
The service combines future-oriented next-gen antivirus software with deep learning, the latest AI technology and access credential theft protection plus continuous threat monitoring by cybersecurity experts.
HP Wolf Pro Security provides actionable insights through the HP Wolf Security Controller as well as a powerful analytics platform. Your IT team can monitor the status of your end devices, generate reports and warnings about unprotected end devices as well as receive details about blocked threats—all in one cloud-based dashboard.
Benefits:
- Protect your end devices with enterprise-grade isolation technology.
- Protect your employees against cyber threats without negatively impacting their productivity.
- Monitoring and management by industry-certified security experts.
Only HP Wolf Security combines:

Detect and stop known and unknown threats and phishing attacks (access credential theft) by bolstering protective layers.
- Malware protection

Hardware-based isolation and cloud-based monitoring and intelligence thanks to an advanced next-generation antivirus solution.
- Threat mitigation
- Identity protection.

Real-time threat monitoring with full security analyses and actionable insights.
- Threat evaluation and analysis
- Comprehensive reports

Security experts analyse threats and make recommendations for how to strengthen security.
- Onboarding, policy configuration and implementation
- Continuous threat monitoring and infrastructure hosting
HP Wolf Pro Security provides:
- The security that your end devices are protected
- The simplicity of an outsourced security service
- Real-time relevant insights
- An uninterrupted user experience
Multi-layer protection
Modern tools to protect against the biggest attack vectors.
- Malware protection
- Threat mitigation
- Identity protection
Certified security experts
Supported by our security experts to keep your HR costs down.
- Onboarding, policy configuration and implementation
- Continuous threat monitoring and infrastructure hosting
Actionable insights
Relevant and real-time insights to protect your end devices
- Threat evaluation and analysis
- Comprehensive reports
HP Wolf Pro Security Edition.
The new HP Wolf Pro Security Edition combines threat mitigation and malware prevention for simple IT environments.
The licence can only be purchased in combination with HP hardware.
HP Wolf Security Edition is a pre-configured feature and does not require the setting up or management of a sophisticated IT console.
Benefits:
- A single dashboard for monitoring use – Status, user settings and security warnings.
- Software updates are automatically installed on the PC No user intervention required
- Support is required for the duration of the 1 or 3 year licences.

HP Wolf Pro Security provides:
- The security that your end devices are protected
- The simplicity of an outsourced security service
- Real-time relevant insights
- An uninterrupted user experience
Multi-layer protection
Modern tools to protect against the biggest attack vectors.
- Malware protection
- Threat mitigation
- Identity protection
Certified security experts
Supported by our security experts to keep your HR costs down.
- Onboarding, policy configuration and implementation
- Continuous threat monitoring and infrastructure hosting
Actionable insights
Relevant and real-time insights to protect your end devices
- Threat evaluation and analysis
- Comprehensive reports