

BeyondTrust remote access solution.
Ensuring your enterprise is GDPR compliant.
When the GDPR came into effect on 25 May 2018, all organisations were obliged to introduce and adhere to new data security standards. Once the two year transition period expires, companies will have to follow a set of regulations—and non-compliance will be penalised.
In implementing the necessary data protection provisions, it is imperative that technology is aligned with the highest security requirements. BeyondTrust’s solutions have always focused on security at the heart of their designs. This ensures that every remote access connection made by customers—whether a privileged user connecting to a critical system or a help desk connecting to an end-user’s system—is secure, protecting critical systems and data.
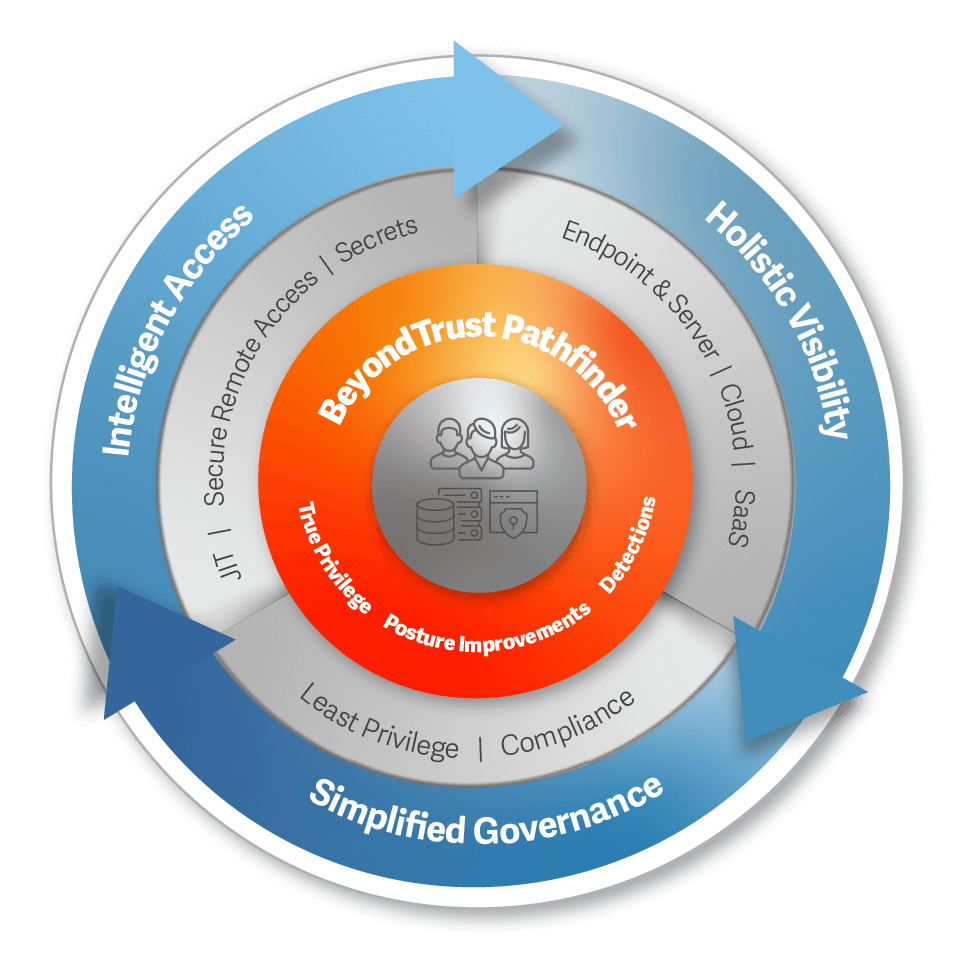
By choosing BeyondTrust remote access solutions, companies can ensure compliance with all GDPR provisions. The BeyondTrust service catalogue includes:
GDPR Pseudonymisation Support – Meet GDPR initiatives through responding to Right to Erasure requests by searching for specific criteria supplied by the requestor.
Improved Customer Agreement Enhancements – Improve security among support teams by reassuring customers they’re dealing with the intended organisation.
Enforce Policy of Least Privilege – Only give access to data to those who need it, when they need it, with granular levels of access controls that eliminate “all or nothing” access.
Manage Privilege ‘Sprawl’ – Identify and secure all your privileged accounts centrally across your organisation, including dormant credentials, eliminate insecure practices of employees sharing or writing down passwords, and integrate your security policies.
Secure and Protect All Privileged Accounts – Store, rotate, and manage privileged credentials within a secure enterprise password vault, and grant access based on job roles and requirements creating a reliable “privilege on demand” workflow.
BeyondTrust’s Secure Access solutions enable businesses to control, monitor, and manage access to critical systems and data, while ensuring that people remain productive and are not impeded in their day to day job tasks. BeyondTrust offers users quick and secure system access that keeps access data safe from prying eyes and protects endpoints against external dangers. BeyondTrust’s implementation uses the “Security by Design” principle from start to finish.
We use YouTube to embed video content on our website. This service may collect data on your activity. For more information, please go to the settings page.
BeyondTrust remote access solution.
Ensuring your enterprise is GDPR compliant.
When the GDPR came into effect on 25 May 2018, all organisations were obliged to introduce and adhere to new data security standards. Once the two year transition period expires, companies will have to follow a set of regulations—and non-compliance will be penalised.
In implementing the necessary data protection provisions, it is imperative that technology is aligned with the highest security requirements. BeyondTrust’s solutions have always focused on security at the heart of their designs. This ensures that every remote access connection made by customers—whether a privileged user connecting to a critical system or a help desk connecting to an end-user’s system—is secure, protecting critical systems and data.
By choosing BeyondTrust remote access solutions, companies can ensure compliance with all GDPR provisions. The BeyondTrust service catalogue includes:
GDPR Pseudonymisation Support – Meet GDPR initiatives through responding to Right to Erasure requests by searching for specific criteria supplied by the requestor.
Improved Customer Agreement Enhancements – Improve security among support teams by reassuring customers they’re dealing with the intended organisation.
Enforce Policy of Least Privilege – Only give access to data to those who need it, when they need it, with granular levels of access controls that eliminate “all or nothing” access.
Manage Privilege ‘Sprawl’ – Identify and secure all your privileged accounts centrally across your organisation, including dormant credentials, eliminate insecure practices of employees sharing or writing down passwords, and integrate your security policies.
Secure and Protect All Privileged Accounts – Store, rotate, and manage privileged credentials within a secure enterprise password vault, and grant access based on job roles and requirements creating a reliable “privilege on demand” workflow.
BeyondTrust’s Secure Access solutions enable businesses to control, monitor, and manage access to critical systems and data, while ensuring that people remain productive and are not impeded in their day to day job tasks. BeyondTrust offers users quick and secure system access that keeps access data safe from prying eyes and protects endpoints against external dangers. BeyondTrust’s implementation uses the “Security by Design” principle from start to finish.




Want to find out more?
Contact Markus Meleka for expert advice.
Phone +49 7132 981-3312